Elevated admin rights for one app only, part deux
- Ok, a different approach : Let's find an app that will elevate a specific app only...

I looked into several different options : Gsudo, JEA through Powershell and to create a task with elevated rights.
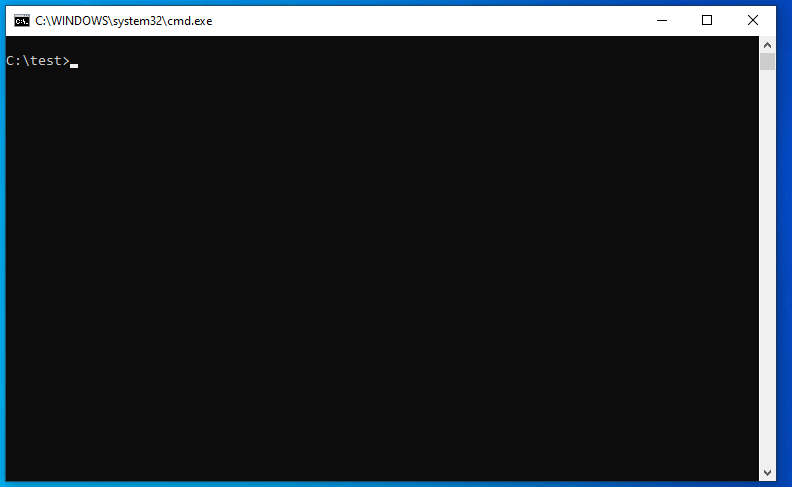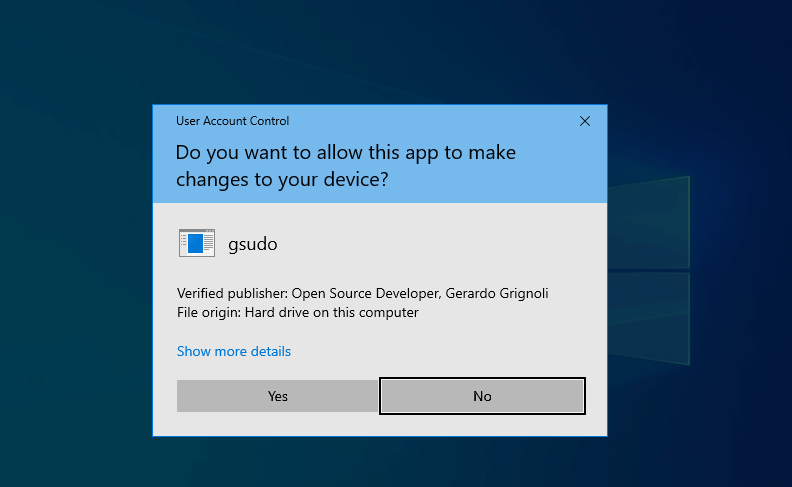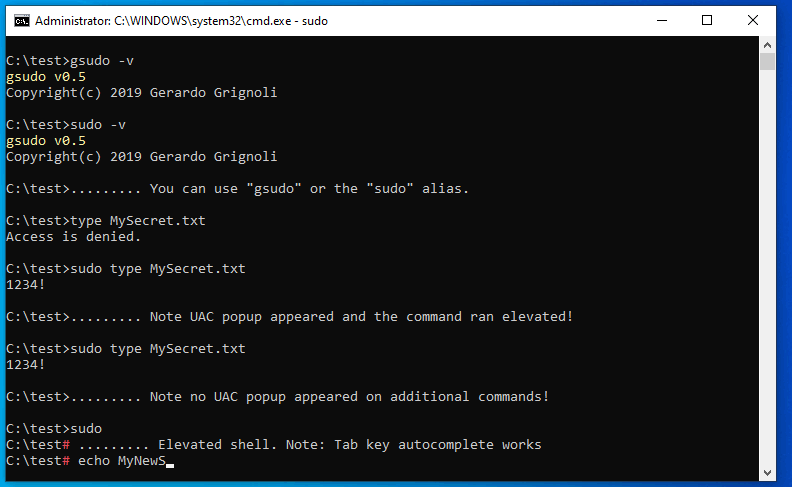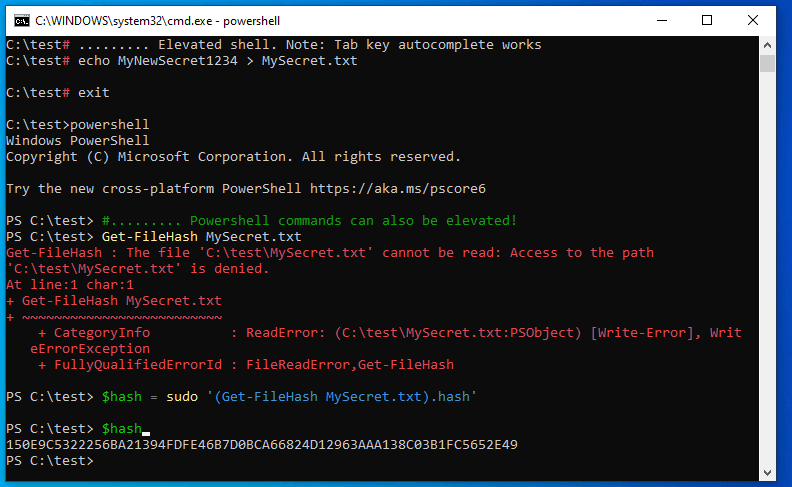
- Gsudo technically worked but for some reason, after creating a shortcut and giving it full rights, if I was to log on as a regular domain user, the UAC popup would present it self... no matter what options that were added or removed.
Just Enough Administration
- JEA or just enough administration is a security technology that enables delegated administration for anything managed by PowerShell. But when it comes to start a process as admin... again, could not get it to go. Here's what I did :
- Created a config folder :
New-PSSessionConfigurationFile -Path C:\JEA- Created a JEAConfig.pssc and this is what I added to it :
@{
SchemaVersion = '2.0.0.0'
SessionType = 'RestrictedRemoteServer'
RunAsVirtualAccount = $true # Runs as a local admin account
ModulesToImport = 'JEACommands'
VisibleCmdlets = @('Start-Process')
}- Created a PWSH module folder :
New-Item -Path "C:\Program Files\WindowsPowerShell\Modules\JEACommands" -ItemType Directory- Created a module script that I saved in that folder called : JEACommands.psm1
function Start-Launcher {
Start-Process -FilePath "C:\Path\To\launcher.exe" -Verb RunAs
}
Export-ModuleMember -Function Start-Launcher- I registered the JEA session :
Register-PSSessionConfiguration -Name LauncherJEA -Path C:\JEA\JEAConfig.pssc -Force- Added Domain Users to the mix :
Set-PSSessionConfiguration -Name LauncherJEA -ShowSecurityDescriptorUI- When I got to this step... I realised that this tool is more for server limited acces :
Enter-PSSession -ComputerName YourServer -ConfigurationName LauncherJEA
Start-Launcher - I modified the last command to see if I could run it localy... It ran fine on the admin side but not on a domain user session...
RunAsTool
- Great tool but it seems to keep the local admin password secured and encrypted somewhere which.... could lead to some hacking... which we cannot afford. https://security.stackexchange.com/questions/278784/how-safe-is-the-runastool-exe-any-known-issues
Let's create something else, based off RunAsTool.
-
So this tool got me thinking : What about a application that uses Privileged Identidy Management of Azure to elevate the rights of that user temporarily?
- Avantages : - Doesn't store the admin password
- Members of a specific group only could have access
- Could configure MFA
- Lets us track when the user activated is rights
- Could program it for specific application (like right are only activated when accessing the app)
- Cons : - Need to create the backend to make it happen
- Make an app?
- Might have to change some local computer configurations
- Avantages : - Doesn't store the admin password
-
First thing I did : Create a group with users that will have to activate their PIMs
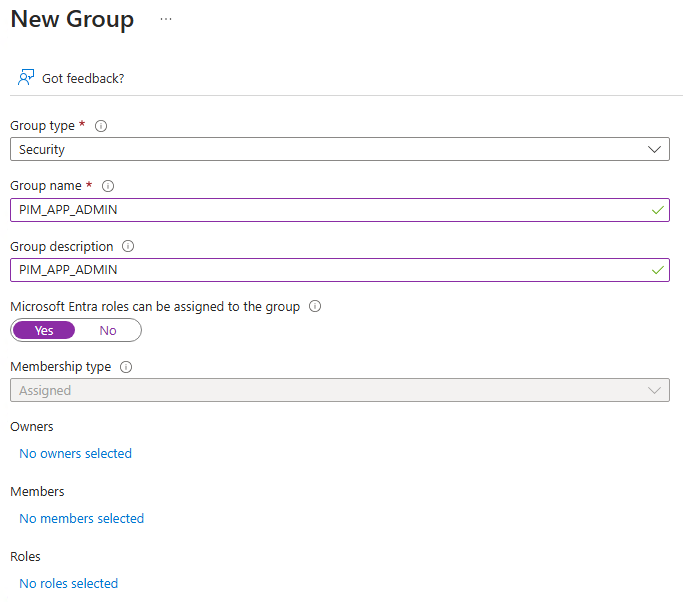
- Owners : Myself or an admin (Idealy a global admin)
- Members : That's where I'll need to add the final group but for now, I put a couple of non-admins
- No Roles since they will not need to have Azure roles... at least I think.
-
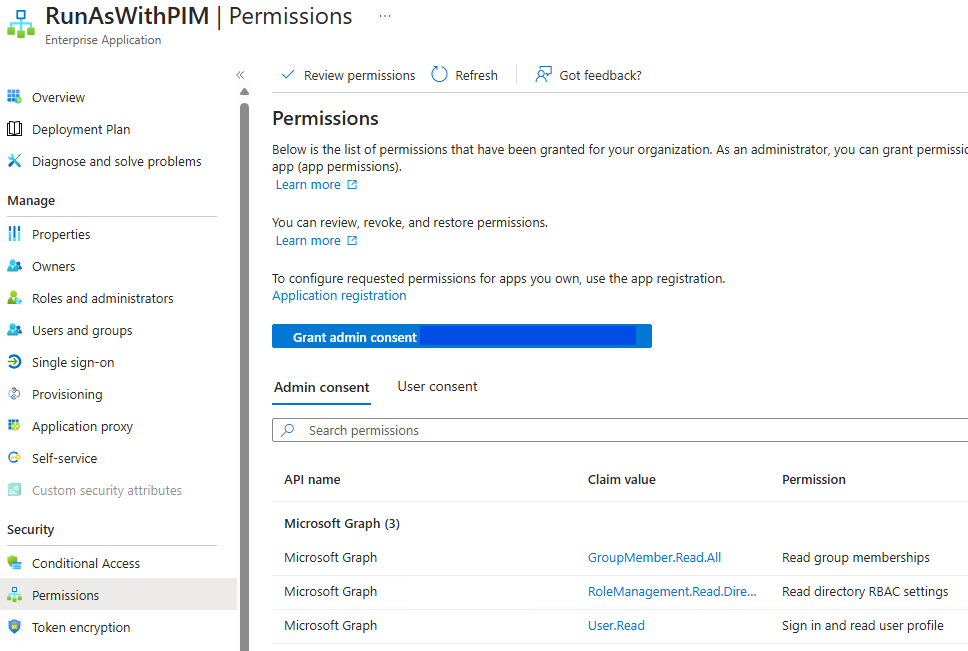
Toying aroung with a python script, I created an app ...ish that calls a Graph API (Azure). That app has to exist in Azure and have the proper role installed :